

After having upgraded my Pi-Hole to v6, for some reason yesterday it started to not recognize any of the blocklists. So, I resetted it and now it works.


After having upgraded my Pi-Hole to v6, for some reason yesterday it started to not recognize any of the blocklists. So, I resetted it and now it works.


Just gonna leave this here.


I use NewPipe that also can’t play age-restricted videos at the moment. I didn’t say that I was using something that works, just that I don’t trust revanced so much.


I like revanced but it is still the closed source YouTube client and I still don’t know what it is doing. Plus you have to connect a Google account for some actions (like history).
Unfortunately, many of the cars transmit the surveillance data through phone carrier data lines, using an embedded SIM card. So, sadly I don’t think this would help very much.


Yes, this is it. I bought it because it was cheap (100€) and had a built-in CPU. The only problems are that it hasn’t got many SATA or PCIe ports. This is fine however, because I have no need for them right now.



This is a custom built mini PC, with a mini-ITX motherboard and an Intel N100 CPU. It gets powered by a power supply that I got from an old computer. Also, it needs no active cooling, just a heatsink. It almost never gets above 60°C.
(and yes, it has no case).
In it I run:


Is it just me, or have I seen like 6-7 of these posts at this point?


Oh, I missed the L1 in the title. Basically, all the decryption at L1 is happening inside a Trusted Execution Environment. This is a dedicated chip that does all encryption-decryption (among other things). This is why it is so difficult to extract the keys, because they don’t enter the CPU or are stored in RAM, because the dedicated chip handles all of these.
So I don’t think you can find a guide about this, because if anyone has found even one exploit, they would be keeping it to ourselves, so that it doesn’t get patched.
Although it is very difficult, I think the only real solution is to reverse engineer a TEE and find an exploit yourself.
If you manage to do this, please let me know! I am happy to get updates about progress in this topic.


I have heard about a TamperMonkey userscript called EMELogger that logs some information about EME, in the web tools console making it easier to get the PSSH. I haven’t tried it though.
Also, I don’t think you will find guides on paid content as this is considered highly illegal (I think).
I managed to fix this problem by pointing my domain name to my private IP address (with pihole’s local DNS entries), so I could access it. Then, I just got certs for the domain and applied them with nginx.
I know, but for some reason my router does not let me access my domain (with duckdns) when connected to my network. So even if I get certs for the domain, I will not be able to access it. I have set up local DNS entries (with Pi-Hole) to point to my srrver, but I don’t know if it possible to get certs for that, since it is not a real domain.
EDIT: Fixed it. (See reply for fix)
I installed Void Linux on my Raspberry Pi without looking at the details, and I was surprised that it had no systemd! It was the first non-systemd distro that I had encountered and also pretty fast.


Sad it does not support Invidious. Else I would be using it.


(I don’t have time to make an image right now, but anyway)
Hey America, how you doing?
Don’t keep your gun in the oven.
Oh.


So, OP has 45.57 gold medals only for his first torrent on the list?


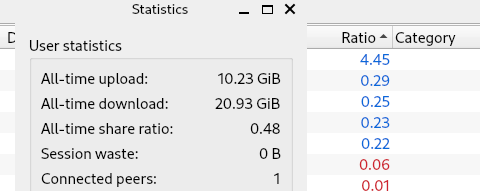
I am waiting for my medal


make 8 million computers crash
other companies say you’re trash
blame others
cry


Yes, basically on internal LAN I put admin admin to everything.
My laptop is called xontros-gatos, which in my native language means fat-cat. Similarly, my server is called server-cat, a small laptop that I have for testing stuff is called small-cat and a new laptop that I just got is called fatter-cat.
I LIKE CATS I LIKE CATS I LIKE CATS I LIKE CATS I LIKE CATS I LIKE CATS I LIKE CATS I LIKE CATS