

You’re going to have to read every single release with breaking changes.


You’re going to have to read every single release with breaking changes.


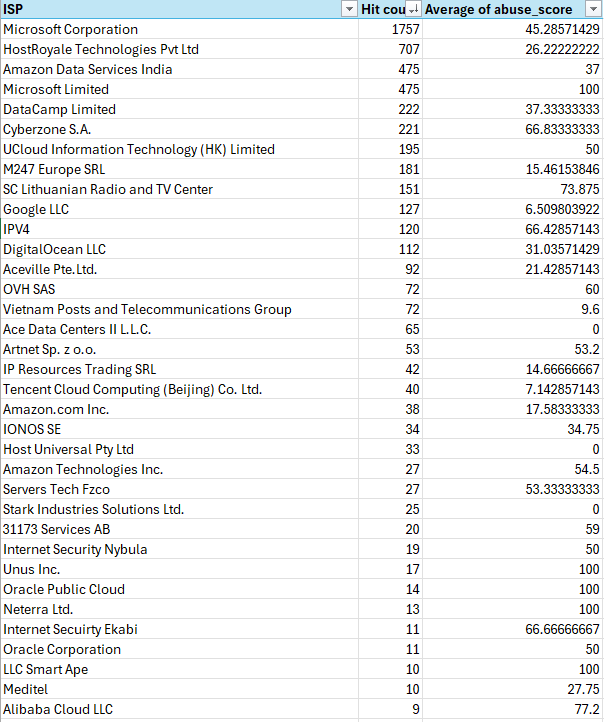
I’m trying to block the most likely attack vectors which is definitely VPS providers at this point in time. I just figure if I am blocking subnets plus additionals I identify it will force them out of these vectors to attack in ways I might be able to report better abuse.
Here check out my analysis.


No I think f2b handling it would be totally fine for me. Kids got in the way with digging around too much but will try this week.


Ahhhmazing, I’ll set this up tonight. Really appreciate the help.


I’ve used it on a machine before but given I am using a cloudflared container for ingress, can I route my traffic through a f2b container to the app? This might be ideal from a co fig perspective.
LLMs say yes but I’ll need to play around.


I have more than 50k but even that page doesn’t recommend it.
Top of that page
Recommendation: Use WAF custom rules instead
Cloudflare recommends that you create WAF custom rules instead of IP Access rules to perform IP-based or geography-based blocking (geoblocking):
- For IP-based blocking, use an IP list in the custom rule expression.
On the fail2ban front, can I run my traffic through a f2b container and out into my app?


How easy is it to configure?
My goal is to download some lists from github and generate one big ban list to feed into the WAF but the community lists of Crowdsec might negate the need.


I use namesilo for everything but my .au domains.


Sometimes I miss my r720s but the silence is nice now.
Xcp or proxmox as your os.
720 depending on chips and memory is great for game servers.


Download your the Amazon UI or use this tool while you can though.


Just a warning the Download and transfer via USB will no longer be an option from 26th of Feb according to Amazon UI.


I didn’t think OP was going the ZFS route so it wouldn’t matter on that point.
His Server 2 will be running on the red line imho so any overhead would have impact.


Mount your NFS in the fstab and make sure you have docker set to wait until the mount is working. Here is a guide. https://davejansen.com/systemctl-delay-start-docker-service-until-mounts-available/
I’ve only had to delay on my N100s.
So I have the mounts set and then just use those paths in my compose. All my machines have the same paths.


quicksync should let the i3 handle jellyfin just fine if you’re not going beyond 1080p for a couple of concurrent users. Especially if you configure the Nice values to prefer jellyfin over immich.
Most of my content is 4K h264. You may be right on the 1080 but I don’t have content at that resolution generally.
Worst case scenario he can always keep the N300 for other stuff if it doesn’t work out.


I’ve looked at it but never actually given the Synology proxy a go despite using their DNS server. Does it do auto certificate renewal?
Have you considered using a Cloudflare tunnel to bypass the CGNAT? You can do that into a proxy or straight into the service.


That would be a smart move on their behalf I think.


Might be the population on lemmy but elsewhere docker or podman are way more common. K8 in Enterprise.


I ran Jellyfin on a N100 for a while and it just couldn’t cope despite being by itself on the machine. I mostly watch 4K h264 encoded stuff. I ended up putting it on a machine with an i5.


All the services OP has listed run great in docker, excluding Frigate (not tested personally).
I’d rather not have them probing my website at all. I’m not Facebook, my data is not unlimited and free.